The Remote Work Security Gap No One Talks About
Published on: 06/01/2026
Remote work has been a game-changer. Lower overhead. Happier employees. Wider talent pool. All wins.
Protect Your Business

Remote work has been a game-changer. Lower overhead. Happier employees. Wider talent pool. All wins.

Not every cyber risk comes from the outside. Some walk right in the front door ... in the form of tools, apps, and devices your own employees are using without asking. It’s called shadow IT. And it’s probably already happening in your business.

Cybersecurity threats don’t stand still. They adapt. They get smarter. And every time technology takes a step forward, attackers figure out how to twist it to their advantage.
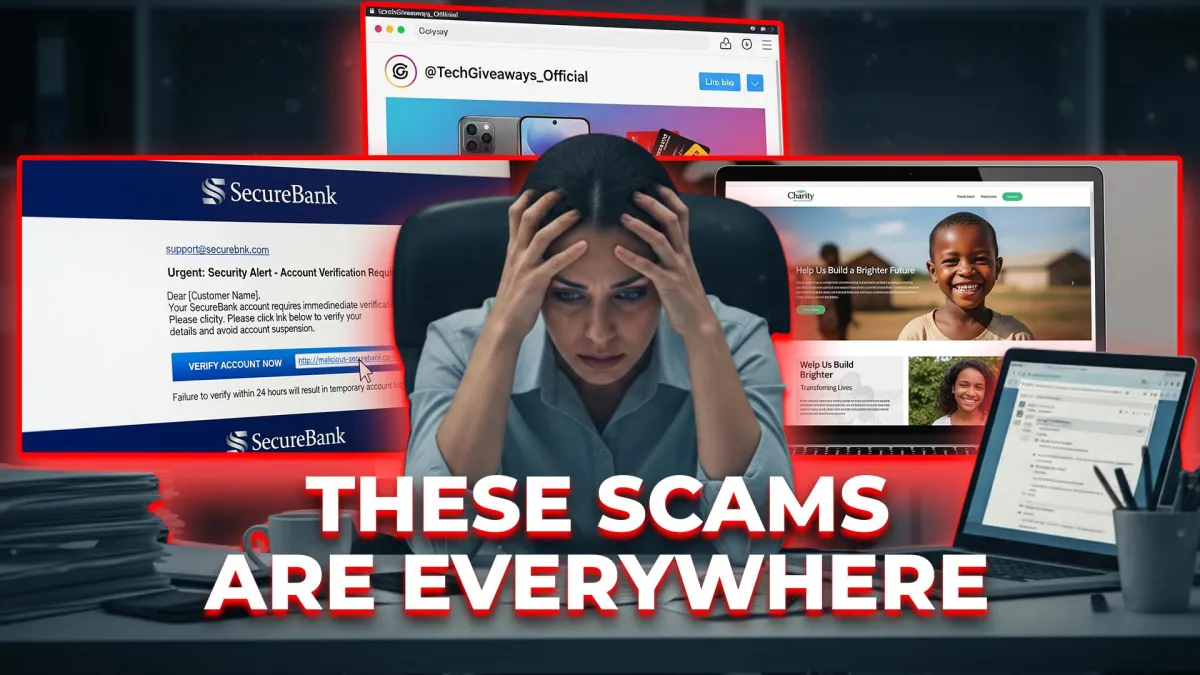
Cybercriminals don’t take days off ... and they don’t wait for a “good” time to strike. They prey on moments when people are busy, distracted, or rushing.